Lessons from yesterday's 27M hack
The hack happened on Penpie, a subDAO of the Penple platform. What happened and what can we learn from it?
I genuinely feel sorry for everyone affected by this exploit, especially those who lost their funds and the Penpie team who worked hard to build their platform. It's heartbreaking to see the impact that such vulnerabilities can have on both individual investors, the entire project, and the DeFi ecosystem.
Despite this setback, it's important to recognize the significant contributions both Penpie and Pendle have made to advancing the DeFi ecosystem. Fortunately, the funds on the main Pendle platform were unaffected by this exploit.
Michiel
A quick Summary
On September 3, 2024, Penpie, a subDAO (Decentralized Autonomous Organisation), operating on the Pendle platform (a protocol for trading tokenized yield), fell victim to a severe exploit that resulted in the loss of $27 million. The incident shows not only the technical vulnerabilities within smart contracts but also underscores the importance of acting on identified risks. In this article, we’ll explore the mechanics of the exploit, the audit, and the broader implications.
The Exploit: What Happened?
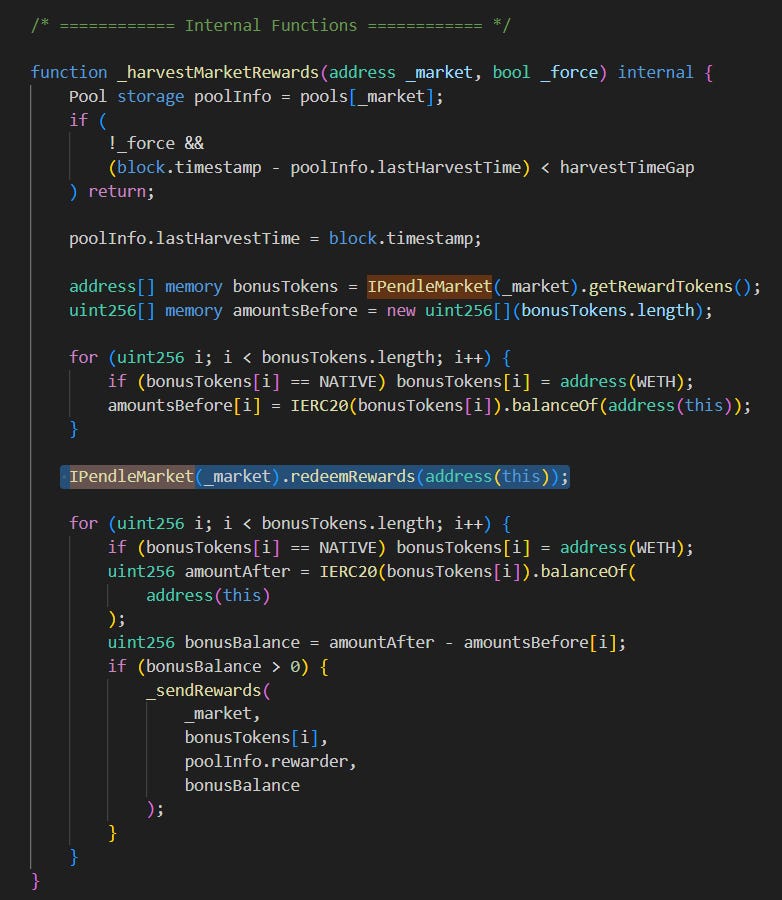
The attack centered around a vulnerability in the internal _harvestMarketRewards function of the PendleStakingBaseUpg contract of Penpie. This function is responsible for harvesting rewards from various markets and distributing them accordingly. The attacker exploited a (kind of) reentrancy vulnerability, allowing them to repeatedly call the function and withdraw far more rewards than they were entitled to.
The vulnerability was rooted in how the function interacted with the redeemRewards method of the IPendleMarket contract:
IPendleMarket(_market).redeemRewards(address(this));This external call allowed the attacker’s malicious contract to manipulate the flow of execution, re-enter the function, and trick the contract into thinking it had more rewards to distribute than it actually did. By artificially inflating the balance of rewards, the attacker managed to drain the contract, causing significant financial loss.
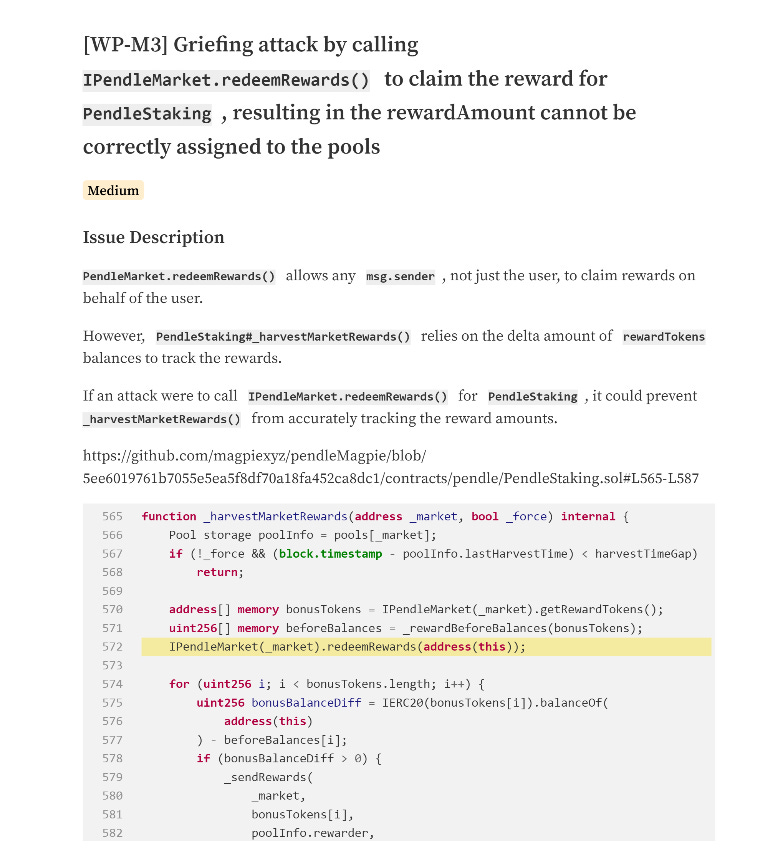
A Known Issue
In June 2023, an audit conducted by WatchPlug flagged a related issue with the same piece of code. The auditors identified that the redeemRewards function call allowed any sender to claim rewards on behalf of the user, potentially leading to inaccurate reward tracking if manipulated.
Despite this critical finding, the vulnerability was not adequately addressed, leaving Penpie exposed to the very attack that WatchPlug had warned about over a year earlier. The issue was marked as resolved. However, in the audit the repo /pendleMagpie was mentioned while I found the exploited code in repo /penpie_contracts. Therefore, I couldn’t check how the vulnerability was addressed.
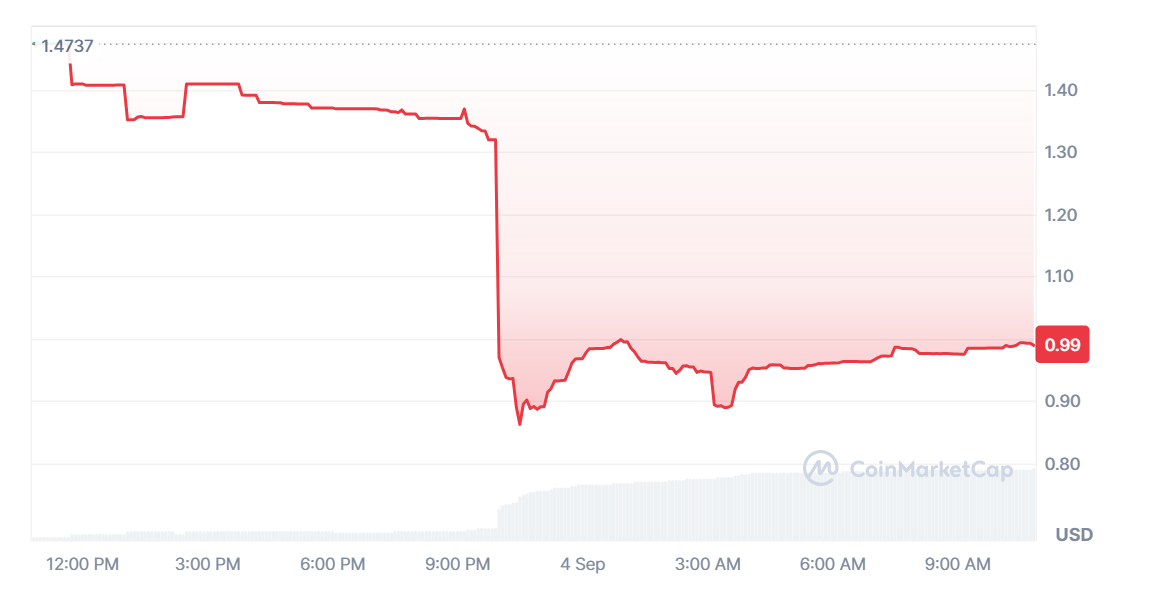
Market Reaction and Implications
The exploit led to a dramatic 40% drop in Penpie’s native token (PNP) and an 8% decline in Pendle’s token (PENDLE). The incident not only shook investor confidence but also started discussions again about the importance of good and responsive security practices in the DeFi space.
Lessons Learned
Act on Audit Findings: It is crucial for DeFi projects to take audit findings seriously and implement recommended changes promptly. The Penpie incident demonstrates the potential consequences of ignoring or delaying such actions.
Reentrancy Guards and Security Best Practices: Ensuring that smart contracts are protected against reentrancy attacks, using tools like reentrancy guards, is essential. So not only on external functions that call internal functions. If there is an internal function making an external call, please be cautious and take adequate steps to secure this call. Additionally, following best practices such as the Check-Effects-Interactions pattern can mitigate many common vulnerabilities.
Ongoing alertness: As DeFi protocols continue to evolve, continuous monitoring and regular audits are necessary to maintain security. The dynamic nature of the crypto space requires projects to stay ahead of potential threats.
Conclusion
The Penpie exploit serves as a harsh reminder that even well-documented vulnerabilities can lead to catastrophic outcomes if not addressed. For the DeFi space to thrive, developers and project teams must prioritize security at every stage, from initial development through to post-deployment monitoring. By learning from incidents like this, the community can work towards a more secure and resilient ecosystem.
Michiel